RemoteIoT SSH AWS Example is a powerful solution for managing and securing IoT devices remotely through AWS infrastructure. In today's rapidly evolving digital landscape, the Internet of Things (IoT) plays a crucial role in connecting devices and enabling seamless communication between them. As businesses increasingly adopt IoT technologies, the need for secure and efficient remote management becomes paramount.
With the integration of SSH (Secure Shell) into AWS services, organizations can enhance the security and reliability of their IoT ecosystems. This guide will delve into the intricacies of RemoteIoT SSH AWS Example, providing actionable insights and practical advice for developers and IT professionals alike.
Whether you're a beginner exploring IoT capabilities or an experienced professional seeking advanced configurations, this article aims to equip you with the knowledge necessary to leverage AWS for remote IoT management. Let's dive into the world of secure IoT operations!
Read also:Emily Compagno Divorce The Full Story Behind The Headlines
Table of Contents:
- Biography of RemoteIoT SSH AWS Example
- Overview of RemoteIoT SSH AWS
- Setting Up RemoteIoT SSH on AWS
- Enhancing Security with SSH
- Tools and Technologies Used
- Benefits of Using RemoteIoT SSH AWS
- Challenges and Solutions
- Real-World Examples
- Optimizing RemoteIoT SSH AWS Performance
- Future Trends in RemoteIoT SSH AWS
Biography of RemoteIoT SSH AWS Example
RemoteIoT SSH AWS Example represents a cutting-edge approach to managing IoT devices in a secure and scalable manner. Below is a summary of key details about this technology:
| Feature | Details |
|---|---|
| Technology Name | RemoteIoT SSH AWS Example |
| Primary Function | Remote management of IoT devices using AWS infrastructure |
| Security Protocol | SSH (Secure Shell) |
| Cloud Platform | AWS (Amazon Web Services) |
| Target Audience | IoT developers, system administrators, and IT professionals |
Overview of RemoteIoT SSH AWS
RemoteIoT SSH AWS is designed to provide a secure and reliable method for managing IoT devices remotely. By leveraging AWS services, users can establish encrypted connections between IoT devices and cloud servers, ensuring data integrity and privacy.
Key Components of RemoteIoT SSH AWS
- Secure Shell (SSH): A cryptographic network protocol that facilitates secure communication over unsecured networks.
- AWS IoT Core: A managed cloud service that allows connected devices to interact with cloud applications and other devices.
- AWS EC2 Instances: Virtual servers in the cloud that can host SSH-enabled IoT applications.
Together, these components create a robust framework for remote IoT management, addressing the challenges of scalability, security, and performance.
Setting Up RemoteIoT SSH on AWS
Setting up RemoteIoT SSH on AWS involves several steps, each crucial for ensuring a secure and efficient environment. Below is a detailed guide to help you through the process:
Step 1: Create an AWS Account
Begin by signing up for an AWS account if you haven't already. AWS offers a free tier that includes many essential services, making it an ideal starting point for beginners.
Read also:Ron Jeremy Jail The Untold Story And Legal Journey
Step 2: Configure AWS IoT Core
Once your account is ready, set up AWS IoT Core to manage your IoT devices. This involves creating certificates, policies, and rules to govern device behavior.
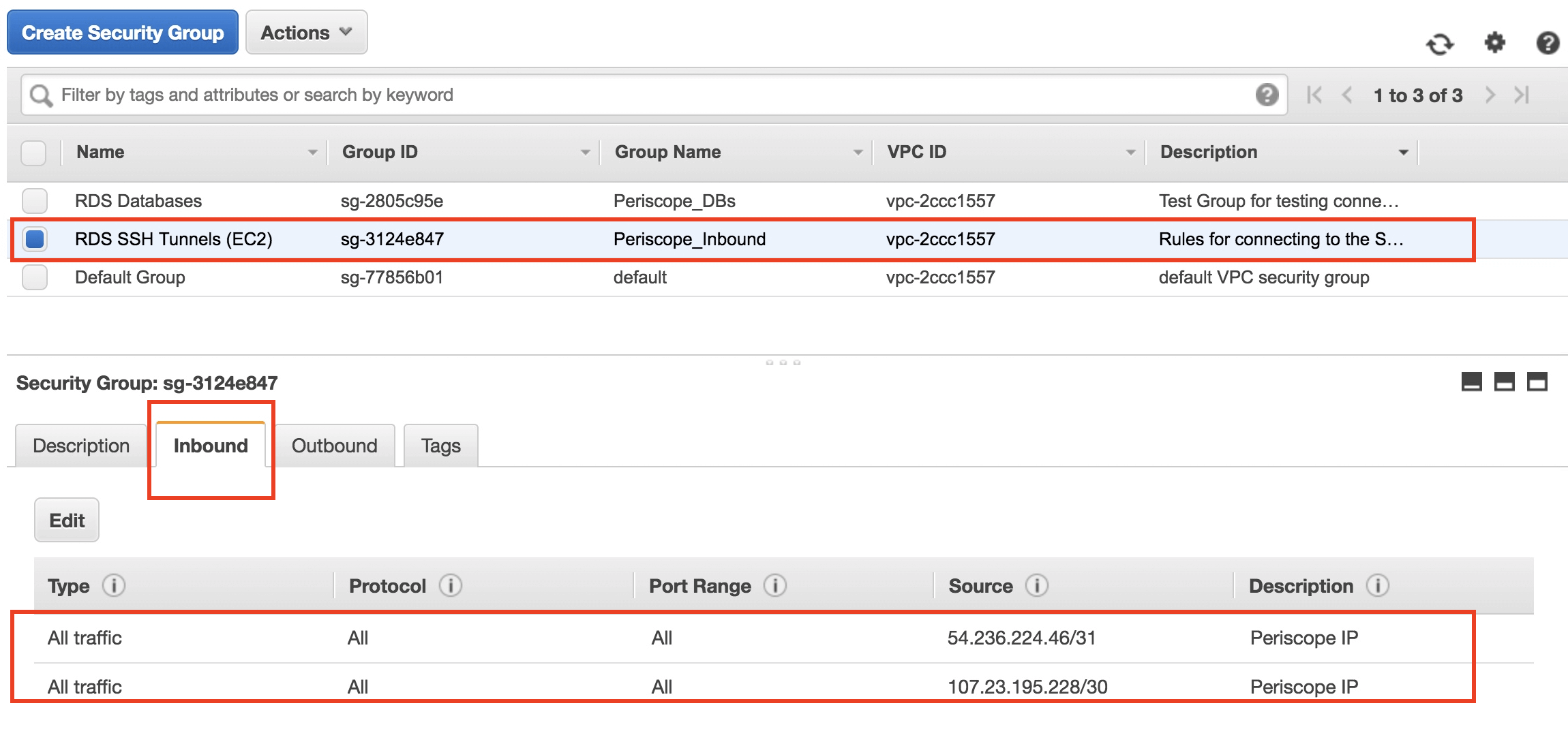
Step 3: Launch an EC2 Instance
Launch an EC2 instance to serve as the server for your SSH connections. Ensure that the instance is configured with the appropriate security groups to allow SSH traffic.
Step 4: Connect IoT Devices
Finally, connect your IoT devices to AWS IoT Core and establish SSH connections to the EC2 instance. This completes the setup process, enabling remote management of your IoT ecosystem.
Enhancing Security with SSH
Security is a top priority when managing IoT devices remotely. SSH offers several features that enhance the security of your RemoteIoT SSH AWS setup:
- Encryption: SSH encrypts all data transmitted between devices and servers, protecting sensitive information from unauthorized access.
- Authentication: SSH supports various authentication methods, including password-based and public key authentication, ensuring only authorized users can access the system.
- Integrity: SSH ensures data integrity by detecting and preventing tampering during transmission.
By implementing these security measures, organizations can safeguard their IoT infrastructure against potential threats.
Tools and Technologies Used
Several tools and technologies are integral to the success of RemoteIoT SSH AWS implementations:
1. AWS IoT Core
AWS IoT Core simplifies the process of connecting and managing IoT devices, providing a scalable platform for IoT applications.
2. AWS EC2
AWS EC2 offers flexible computing capacity in the cloud, enabling users to host SSH-enabled IoT applications with ease.
3. SSH Clients
SSH clients such as PuTTY (for Windows) and OpenSSH (for Linux and macOS) facilitate secure connections to remote servers, streamlining IoT device management.
Benefits of Using RemoteIoT SSH AWS
Adopting RemoteIoT SSH AWS brings numerous advantages to organizations looking to enhance their IoT capabilities:
- Improved Security: SSH ensures secure communication between devices and servers, protecting against cyber threats.
- Scalability: AWS infrastructure supports large-scale IoT deployments, accommodating growing business needs.
- Cost Efficiency: By leveraging cloud services, organizations can reduce infrastructure costs while maintaining high performance.
These benefits make RemoteIoT SSH AWS an attractive solution for businesses seeking to optimize their IoT operations.
Challenges and Solutions
Despite its advantages, implementing RemoteIoT SSH AWS comes with its own set of challenges:
Challenge 1: Complex Setup
Solution: Follow comprehensive guides and documentation provided by AWS to streamline the setup process.
Challenge 2: Security Threats
Solution: Implement robust security measures, such as firewalls and intrusion detection systems, to fortify your IoT infrastructure.
Challenge 3: Performance Bottlenecks
Solution: Optimize your AWS resources and configurations to ensure optimal performance and reliability.
Real-World Examples
Several organizations have successfully implemented RemoteIoT SSH AWS to enhance their IoT operations:
Example 1: Smart Agriculture
Agricultural companies use RemoteIoT SSH AWS to monitor and control irrigation systems, optimizing water usage and increasing crop yields.
Example 2: Industrial Automation
Manufacturing plants leverage RemoteIoT SSH AWS to manage and maintain industrial equipment, reducing downtime and improving efficiency.
Example 3: Smart Cities
Municipalities employ RemoteIoT SSH AWS to monitor traffic patterns, manage public lighting, and enhance urban infrastructure.
Optimizing RemoteIoT SSH AWS Performance
To maximize the performance of your RemoteIoT SSH AWS setup, consider the following strategies:
- Monitor Resource Usage: Regularly analyze resource consumption to identify and address performance bottlenecks.
- Automate Routine Tasks: Use automation tools to streamline repetitive tasks, freeing up resources for more critical operations.
- Implement Load Balancing: Distribute traffic evenly across multiple servers to prevent overload and ensure consistent performance.
By applying these optimization techniques, organizations can enhance the efficiency and reliability of their RemoteIoT SSH AWS implementations.
Future Trends in RemoteIoT SSH AWS
The future of RemoteIoT SSH AWS looks promising, with several emerging trends set to shape its evolution:
- Edge Computing Integration: Combining edge computing with AWS services will enable faster data processing and reduced latency.
- AI and Machine Learning: Incorporating AI and machine learning into IoT systems will enhance predictive capabilities and decision-making processes.
- 5G Connectivity: The rollout of 5G networks will provide faster and more reliable connectivity for IoT devices, further enhancing their capabilities.
These trends highlight the potential for RemoteIoT SSH AWS to evolve and meet the growing demands of the IoT ecosystem.
Kesimpulan
In conclusion, RemoteIoT SSH AWS Example offers a powerful solution for managing IoT devices securely and efficiently. By leveraging AWS services and SSH protocols, organizations can enhance the security, scalability, and performance of their IoT operations.
We encourage readers to explore the resources mentioned in this article and experiment with RemoteIoT SSH AWS in their own projects. Don't forget to leave a comment sharing your experiences or questions, and consider subscribing to our newsletter for more insightful content. Together, let's shape the future of IoT technology!