RemoteIoT monitoring has become a cornerstone of modern technology, enabling users to access systems securely from anywhere in the world. With the growing demand for remote access solutions, the ability to download SSH clients for Macs has become crucial for individuals and businesses alike. In this article, we will explore the concept of RemoteIoT monitoring, its benefits, and how you can leverage SSH on Mac for free.
Whether you're a tech enthusiast or a professional looking to enhance your remote access capabilities, understanding the nuances of RemoteIoT monitoring and SSH can significantly improve your workflow. This guide will delve into the tools, methods, and best practices to help you get started.
As the world increasingly shifts toward remote operations, the importance of secure and efficient remote access cannot be overstated. This article will serve as your comprehensive resource for everything related to RemoteIoT monitoring and SSH downloads for Mac, ensuring you have the knowledge to make informed decisions.
Read also:Who Is Adam Schiffs Spouse A Comprehensive Look At Her Life And Influence
Understanding RemoteIoT Monitoring
What is RemoteIoT Monitoring?
RemoteIoT monitoring refers to the practice of accessing and managing Internet of Things (IoT) devices from a remote location. This technology allows users to control, monitor, and analyze IoT devices without being physically present. The integration of IoT with remote monitoring has revolutionized industries such as manufacturing, healthcare, and agriculture.
- Enhances operational efficiency
- Reduces the need for on-site visits
- Improves data collection and analysis
Benefits of RemoteIoT Monitoring
Implementing RemoteIoT monitoring offers numerous advantages, including:
- Cost savings through reduced travel expenses
- Real-time data access for informed decision-making
- Improved system reliability and uptime
By leveraging RemoteIoT monitoring, businesses can achieve greater flexibility and scalability in their operations.
SSH: The Secure Shell Protocol
What is SSH?
SSH, or Secure Shell, is a cryptographic network protocol designed for secure communication over unsecured networks. It provides a secure channel for remote access, file transfer, and command execution between devices. SSH is widely used in IT environments due to its robust security features.
Why Use SSH for RemoteIoT Monitoring?
SSH is an ideal choice for RemoteIoT monitoring because it ensures:
- Data encryption to protect sensitive information
- Authentication mechanisms to verify user identities
- Reliable and secure connections for remote access
These features make SSH a trusted solution for managing IoT devices remotely.
Read also:Marguerite Whitley The Fascinating Life And Legacy Of A Hollywood Icon
Downloading SSH for Mac Free
How to Download SSH for Mac
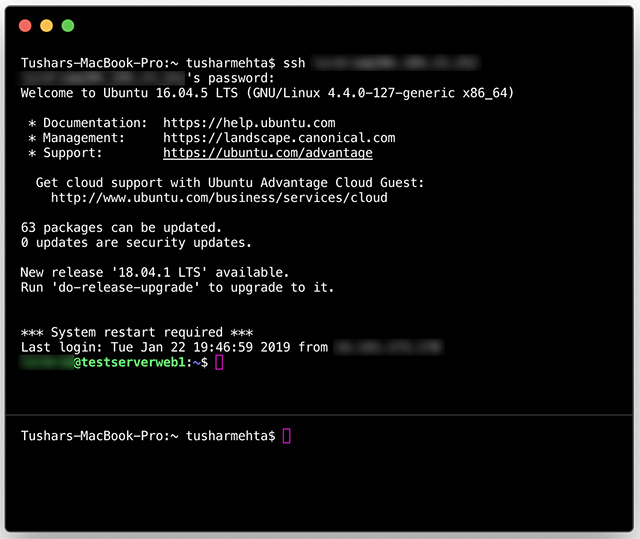
Mac users can access SSH through the built-in Terminal application, eliminating the need for additional downloads. However, if you prefer a graphical user interface (GUI), there are several free SSH clients available for Mac. Below are the steps to download SSH for Mac:
- Open the Terminal application on your Mac.
- Type "ssh" in the command line to confirm its availability.
- For GUI options, visit trusted websites to download free SSH clients like PuTTY or MobaXterm.
Recommended Free SSH Clients for Mac
Here are some of the best free SSH clients for Mac:
- Termius: A cross-platform SSH client with a user-friendly interface.
- Cyberduck: A popular open-source client for file transfers and SSH connections.
- MacSSH: A lightweight and efficient SSH client specifically designed for Mac users.
Setting Up SSH for RemoteIoT Monitoring
Configuring SSH on Mac
Setting up SSH on a Mac involves a few simple steps:
- Enable the Remote Login feature in System Preferences > Sharing.
- Create a public-private key pair using the Terminal command: "ssh-keygen -t rsa".
- Copy the public key to the remote server using the command: "ssh-copy-id username@remote_host".
Best Practices for Secure SSH Connections
To ensure secure SSH connections, follow these best practices:
- Use strong, unique passwords or passphrase-protected keys.
- Disable password authentication and rely on key-based authentication.
- Regularly update SSH software to patch vulnerabilities.
RemoteIoT Monitoring Tools
Top Tools for RemoteIoT Monitoring
Several tools are available to facilitate RemoteIoT monitoring. Some of the most popular ones include:
- PRTG Network Monitor: A comprehensive monitoring solution for IoT devices.
- ThingsBoard: An open-source IoT platform for data visualization and device management.
- DevicePilot: A user-friendly tool for monitoring and managing IoT fleets.
Integrating SSH with RemoteIoT Monitoring Tools
Integrating SSH with RemoteIoT monitoring tools enhances their functionality by providing secure access to IoT devices. This integration allows users to perform tasks such as:
- Configuring device settings remotely.
- Updating firmware and software.
- Diagnosing and troubleshooting issues.
Security Considerations for RemoteIoT Monitoring
Common Security Risks in RemoteIoT Monitoring
While RemoteIoT monitoring offers numerous benefits, it also introduces potential security risks. These risks include:
- Data breaches due to weak authentication.
- Unauthorized access to IoT devices.
- Malware attacks targeting remote connections.
How SSH Mitigates These Risks
SSH plays a critical role in mitigating security risks associated with RemoteIoT monitoring by:
- Encrypting data transmissions to prevent interception.
- Verifying user identities through strong authentication methods.
- Providing a secure tunnel for remote access.
Case Studies: Successful RemoteIoT Monitoring Implementations
Case Study 1: Smart Agriculture
In the agriculture industry, RemoteIoT monitoring has enabled farmers to optimize crop yields by remotely monitoring soil moisture, temperature, and humidity levels. By integrating SSH for secure data access, farmers can make real-time adjustments to irrigation systems and other equipment.
Case Study 2: Healthcare
Healthcare facilities use RemoteIoT monitoring to track patient vital signs and medical device performance. SSH ensures that sensitive patient data remains secure during remote access, maintaining compliance with healthcare regulations.
Future Trends in RemoteIoT Monitoring
Emerging Technologies in RemoteIoT Monitoring
The future of RemoteIoT monitoring is shaped by emerging technologies such as:
- Artificial intelligence for predictive maintenance.
- Blockchain for enhanced data security.
- 5G networks for faster and more reliable connections.
The Role of SSH in Future Developments
As technology continues to evolve, SSH will remain a vital component of RemoteIoT monitoring. Its adaptability and security features will ensure its relevance in future developments, providing a foundation for secure and efficient remote access solutions.
Conclusion
In conclusion, RemoteIoT monitoring with SSH offers a powerful solution for managing IoT devices remotely. By understanding the principles of SSH and leveraging the right tools, users can enhance their remote access capabilities while maintaining robust security. This guide has provided a comprehensive overview of the topic, equipping you with the knowledge to implement RemoteIoT monitoring effectively.
We encourage you to explore the resources mentioned in this article and share your experiences in the comments section below. Additionally, feel free to browse our other articles for more insights into technology and innovation.
Table of Contents
- Understanding RemoteIoT Monitoring
- SSH: The Secure Shell Protocol
- Downloading SSH for Mac Free
- Setting Up SSH for RemoteIoT Monitoring
- RemoteIoT Monitoring Tools
- Security Considerations for RemoteIoT Monitoring
- Case Studies: Successful RemoteIoT Monitoring Implementations
- Future Trends in RemoteIoT Monitoring
- Conclusion